Configure TLS/SSL
Several NXLog Agent network modules support TLS/SSL encryption to prevent malicious actors from viewing or altering data in transit. See TLS/SSL data transfer for a more detailed look into TLS/SSL encryption. Below, we provide examples of forwarding data with one-way and mutual authentication and receiving data over a secure channel.
Send data with one-way authentication
One-way authentication occurs when the remote host provides a certificate but does not require one from connecting clients. You’ll mostly use this type of authentication when sending data to a hosted SIEM.
This configuration uses the om_http output module to send telemetry data to a remote web server over HTTPS. The server supports one-way authentication, so the module only needs to verify the remote server’s certificate to establish a connection.
<Output siem>
Module om_http
URL https://api.example.com
HTTPSCADir /etc/ssl/certs (1)
</Output>| 1 | The HTTPSCADir directive points to a folder containing a Certificate Authority (CA) certificate that can verify the remote host’s certificate. By default, the om_http module uses the OS root certificate store. |
Send data with mutual authentication
Mutual authentication is required when the remote host provides a certificate and expects one back from connecting clients. This type of authentication is common when sending data to a server within your company network or another NXLog Agent instance.
This configuration uses the om_ssl output module to send telemetry data to a remote server over TCP with TLS/SSL The server requires mutual authentication, so the module must present a certificate during the TLS/SSL handshake.
<Output siem>
Module om_ssl
Host 192.168.1.100:516
CAFile /etc/ssl/certs/rootCA.pem (1)
CertFile %CERTDIR%/client.pem (2)
CertKeyFile %CERTDIR%/client.key (3)
KeyPass password (4)
</Output>| 1 | The CAFile directive specifies the path of the Certificate Authority (CA) certificate. NXLog Agent will use this certificate to verify the remote host’s certificate. |
| 2 | The CertFile directive specifies the path of the local server’s certificate to send during the TLS/SSL handshake. |
| 3 | The CertKeyFile directive specifies the path of the server’s certificate private key. |
| 4 | If the private key is secured with a password, specify it in the KeyPass directive. |
Receive data over a secure channel
NXLog Agent supports TLS/SSL when receiving data over the network. This allows you to implement secure data transfer when receiving telemetry data from remote clients or using NXLog Agent as a relay.
This configuration uses the im_ssl input module to receive telemetry data over a secure TCP channel. The module supports both mutual and one-way authentication.
<Input tcp_ssl>
Module im_ssl
ListenAddr 0.0.0.0:1514
RequireCert TRUE (1)
CAFile /etc/ssl/certs/rootCA.pem (2)
CertFile %CERTDIR%/server.pem (3)
CertKeyFile %CERTDIR%/server.key (4)
KeyPass password (5)
</Input>| 1 | The RequireCert directive specifies whether the remote client must present a certificate during TLS/SSL handshake. |
| 2 | If using mutual authentication, you must configure the CAFile or CADir directive to point to a CA certificate file or folder that can verify the remote host’s certificate. |
| 3 | The CertFile directive specifies the path of the local server’s certificate to send during the TLS/SSL handshake. |
| 4 | The CertKeyFile directive specifies the path of the server’s certificate private key. |
| 5 | If the private key is secured with a password, specify it in the KeyPass directive. |
Specify certificates using the thumbprint
On Windows, NXLog Agent supports specifying certificates by their thumbprint.
Follow these steps to find out a certificate’s thumbprint:
-
Open Windows Certificate Manager (certmgr.msc).
-
Find the relevant certificate and double-click to open it.
-
Switch to the Details tab and scroll down to view the Thumbprint field.
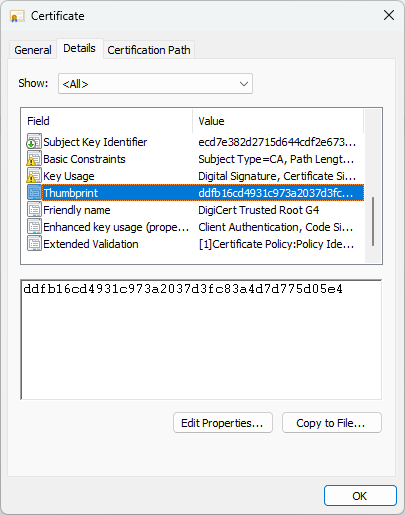
When specifying the local server’s certificate by it’s thumbprint, ensure that the certificate’s private key is exportable. You can check whether a certificate’s private key is exportable by opening it and checking the General tab. If the private key is exportable, the certificate information shows that you have a corresponding private key.
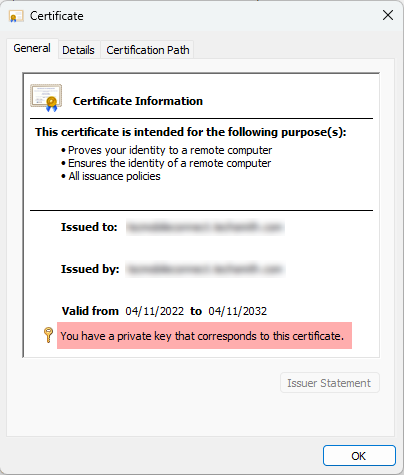
If you’re using encrypted storage or a TPM module where the private key is non-exportable, you must set the UseCNGCertificates directive to TRUE in order to load certificates through the CNG API.
This configuration uses the im_ssl input module to receive telemetry data over a secure TCP channel. It requires two-way authentication and specifies the CA and local server certificates by their thumbprint.
#UseCNGCertificates TRUE(1)
<Input tcp_ssl>
Module im_ssl
ListenAddr 0.0.0.0:1514
RequireCert TRUE(2)
CAThumbprint ddfb16cd4931c973a2037d3fc83a4d7d775d05e4(3)
CertThumbprint ea3ad5c51308d6e13cf288a2676b28c94a41802b(4)
</Input>| 1 | Uncomment this line to load certificates through the CNG API. |
| 2 | The RequireCert directive specifies whether the remote host must present a certificate during TLS/SSL handshake. |
| 3 | The CAThumbprint directive specifies the thumbprint of the CA certificate that can verify the remote host’s certificate. |
| 4 | The CertThumbprint directive specifies the thumbprint of the local server’s certificate to send during the TLS/SSL handshake. |
Specify certificates using a regular expression
On Windows, NXLog Agent supports identifying certificates using a regular expression. This way, you won’t need to reconfigure NXLog Agent when certificates are updated or renewed.
This configuration uses the om_http output module to forward telemetry data to a SIEM. It uses one-way authentication and specifies a regular expression to identify the CA certificate. The regular expression must be PCRE2-compliant.
<Output siem>
Module om_http
URL https://api.example.com
HTTPSCAPattern 'CN=Example Root CA.*OU=www\.example\.com'(1)
</Output>| 1 | The HTTPSCAPattern directive specifies the regular expression to find the appropriate CA certificate to verify the remote host’s certificate. |
