Google Cloud Logging (om_googlelogging)
Google Cloud Logging is a managed service that stores and analyzes log data from applications hosted on Google Cloud and Amazon Web Services.
The Google Cloud Logging API enables you to write logs to Cloud Logging. This module uses the REST version of the API to send events in batches, reducing HTTP response latency, and thus improving data throughput.
| To examine the supported platforms, see the list of installation packages. |
Configuring a Google Cloud service account
om_googlelogging requires a Google Cloud service account and a corresponding private key file in JSON format to connect to the Cloud Logging API. Follow these instructions to create a new service account and download its private key file for an existing project.
-
Log in to your Google Cloud account and switch to the project you want to configure.
-
From the navigation menu, click IAM & Admin > Service Accounts.
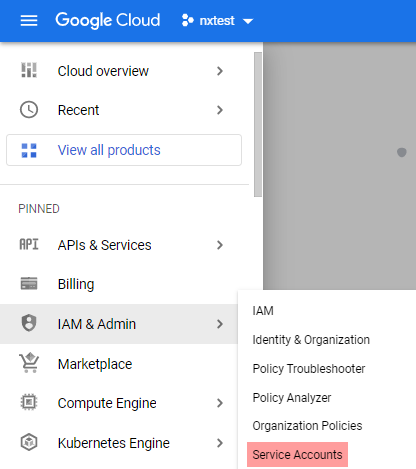
-
Click CREATE SERVICE ACCOUNT.
-
Enter a service account name and description and click CREATE AND CONTINUE.
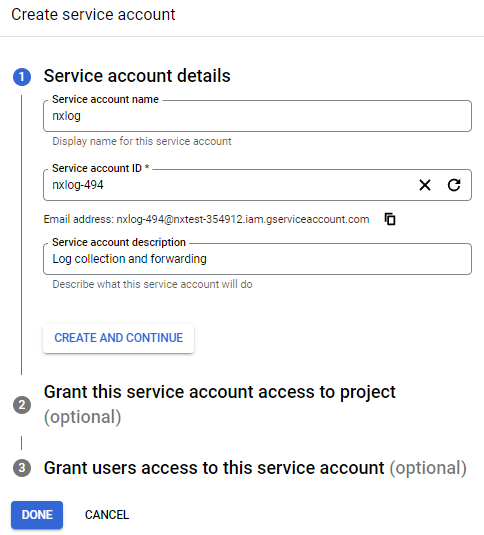
-
Select the Owner role from the Role drop-down and click DONE.
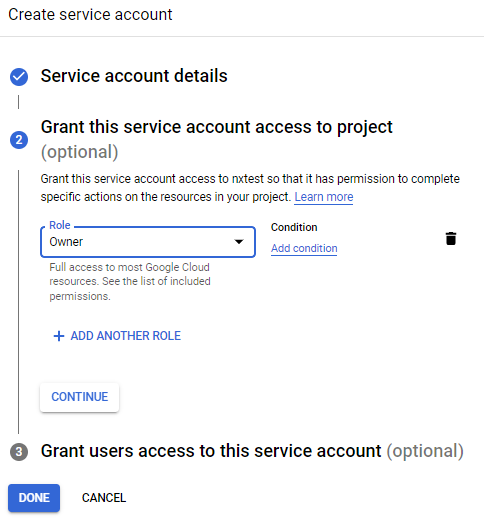
-
Click on the newly created account on the Service accounts page to open its configuration page.
-
Click the KEYS tab, expand the ADD KEY drop-down and select Create new key.
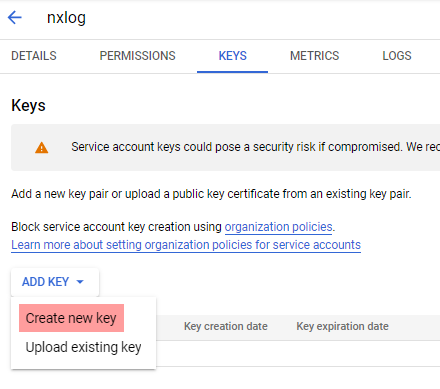
-
Select JSON for the key type and click CREATE to download the private key. Save the private key file to a location accessible by NXLog Agent. This file is required for the NXLog Agent configuration.
Output log format
om_googlelogging forwards the value of the $raw_event field to Google Cloud Logging as JSON payload if it is a valid JSON object.
Otherwise, it sends it as text payload.
If a $Severity field is present, it will use its value to assign a LogSeverity to the record.
If not, it will set the severity to DEFAULT.
The table below lists the possible severity values.
All values are case-insensitive.
| Severity | Alternative values |
|---|---|
|
|
|
- |
|
|
|
|
|
|
|
|
|
|
|
- |
|
|
Alternative values will be translated to the severity value on the left.
Individual JSON log records have the following structure:
{
"jsonPayload": { }, // Value of $raw_event
"severity": "<severity>",
"timestamp": "<EventReceivedTime>"
}Records will have the following structure if the value of $raw_event is not a valid JSON object:
{
"textPayload": " ", // Value of $raw_event
"severity": "<severity>",
"timestamp": "<EventReceivedTime>"
}The complete request body has the following structure:
{
"logName": "<LogName>",
"labels": {
"<key>": "<value>"
},
"resource": {
"type": "<type>"
},
"entries" : [
{
"textPayload": "<raw_event>",
"severity": "<Severity>",
"timestamp": "<EventReceivedTime>"
}
]
}See Method: entries.write in the Google Cloud Logging API reference for more information.
Configuration
|
Data sent with this module must be encoded in UTF-8. Otherwise, the destination will refuse and drop it. If the source does not guarantee that data is UTF-8 encoded, use the xm_charconv extension module to convert it to UTF-8. See Auto-detect and convert character sets in the NXLog Platform User Guide for an example. |
The om_googlelogging module accepts the following directives in addition to the common module directives. The CredentialsFile, LogName, and Resources directives are required.
Required directives
The following directives are required for the module to start.
This mandatory directive specifies the path to the private key file of the service account required for authenticating with the Cloud Logging API. See Configuring a Google Cloud service account for more information. |
|
This mandatory directive specifies the name of the log source on Google Cloud.
It accepts a string in the format |
|
This mandatory group directive specifies the Google Cloud resource that produced the log entry. See resources list to get all available values. For example, specify the monitored resource that owns the database to collect its error logs. |
HTTP(S) directives
The following directives are for configuring HTTP(S) connection settings.
This optional directive can be specified multiple times to add custom headers to each HTTP request. |
|||
This optional directive can be used to enable HTTP compression for outgoing HTTP messages.
The possible values are |
|||
HTTP basic authentication password. You must also set the HTTPBasicAuthUser directive to use HTTP authentication. |
|||
HTTP basic authentication username. You must also set the HTTPBasicAuthPassword directive to use HTTP authentication. |
|||
Specifies if the connection should be allowed with an expired certificate.
If set to |
|||
Specifies if the connection should be allowed without certificate verification.
If set to |
|||
The path to a directory containing certificate authority (CA) certificates. These certificates will be used to verify the certificate presented by the remote host. The certificate files must be named using the OpenSSL hashed format, i.e. the hash of the certificate followed by .0, .1 etc. To find the hash of a certificate using OpenSSL: For example, if the certificate hash is A remote host’s self-signed certificate (which is not signed by a CA) can also be trusted by including a copy of the certificate in this directory. The default operating system root certificate store will be used if this directive is not specified.
Unix-like operating systems commonly store root certificates in In addition, Microsoft’s PKI repository contains root certificates for Microsoft services. |
|||
The path of the certificate authority (CA) certificate that will be used to verify the certificate presented by the remote host. A remote host’s self-signed certificate (which is not signed by a CA) can be trusted by specifying the remote host certificate itself. In case of certificates signed by an intermediate CA, the certificate specified must contain the complete certificate chain (certificate bundle). |
|||
The path of the certificate file that will be presented to the remote host during the HTTPS handshake. |
|||
The path of the private key file that was used to generate the certificate specified by the HTTPSCertFile directive. This is used for the HTTPS handshake. |
|||
Maximum size of the request in bytes. The default is 64 MB. |
|||
This optional directive is used to specify the protocol, IP address (or hostname) and port number of the HTTP or SOCKS proxy host to be used.
The format is |
|||
This optional directive sets the reconnect interval in seconds. If it is set, the module attempts to reconnect in every defined second. If it is not set, the reconnect interval will start at 1 second and double with every attempt. In the latter case, when the system decides that the reconnection is successful, the reconnect interval is immediately reset to 1 sec.
|
|||
This optional directive defines the behavior when the connection with the remote host is lost.
When set to |
Optional directives
A list of key-value pairs for providing event metadata. The labels can be user-defined or system-defined. User-defined labels are optional key-value pairs that you can use to enrich logs.
System-defined labels are defined by Google Cloud Platform (GCP) services for platform logs and are in the format Cloud Logging truncates label keys that exceed 512 B and label values that exceed 64 KB and replaces the truncated text with an ellipsis ( |
Examples
This configuration uses the om_googlelogging output module to forward logs from the project myproject to Google Cloud Logging.
<Output google_logging>
Module om_googlelogging
CredentialsFile /path/to/credentials.json (1)
LogName projects/myproject-343509/logs/test
<Labels> (2)
zone us-central
</Labels>
<Resources> (3)
type gce_instance
</Resources>
</Output>| 1 | Credentials file for authenticating with the Cloud Logging API. See Configuring a Google Cloud service account for more information. |
| 2 | List of labels defined as key-value pairs to attach to the event. |
| 3 | List of resources to attach to the event. |
