RSA NetWitness
The RSA NetWitness SIEM Platform is a threat detection and incident response suite that leverages logs and other data sources for monitoring, reporting, and investigations. NXLog is an officially supported RSA Ready certified product and can be configured as the log collection agent for NetWitness.
Configuring NetWitness
-
Make sure syslog collection is enabled. RSA NetWitness creates Syslog listeners by default for UDP on port 514, TCP on port 514, and SSL on port 6514. See Configure Syslog Event Sources in the NetWitness documentation for further setup notes.
-
Add a Log Decoder using the "Envision Config File" resource.
-
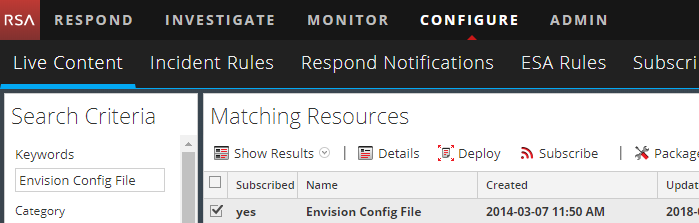
From the NetWitness menu, select Configure > Live Content.
-
In the Keywords field, enter
Envision Config File. -
In the Matching Resources pane, check the Envision Config File entry and click Deploy in the menu bar.
-
In the Deployment Wizard Resources pane, click Next.
-
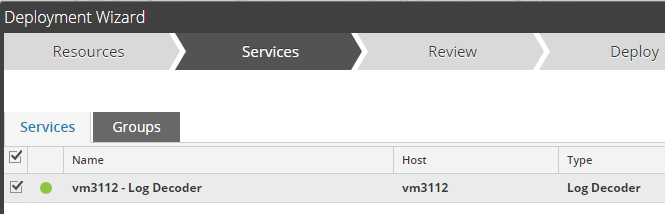
In the Services pane, select the Log Decoder and click Next.
-
In the Review pane, review the changes and click Deploy. Click Close after the deployment task has finished.
-
-
Deploy the Common Event Format.
-
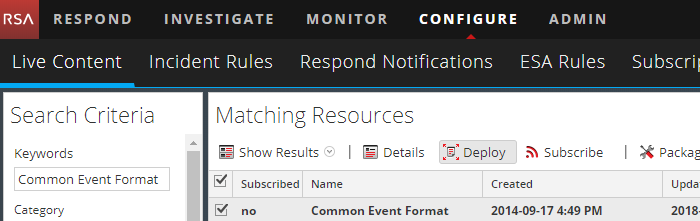
From the NetWitness menu, select Live > Search.
-
In the Keywords field, enter
Common Event Format. -
In the Matching Resources pane, check the Common Event Format entry and click Deploy in the menu bar.
-
In the Deployment Wizard Resources pane, click Next.
-
In the Services pane, select the Log Decoder and click Next.
-
In the Review pane, review the changes and click Deploy. Click Close after the deployment task is finished.
-
-
Ensure that the CEF parser is enabled on the Log Decoder(s).
-
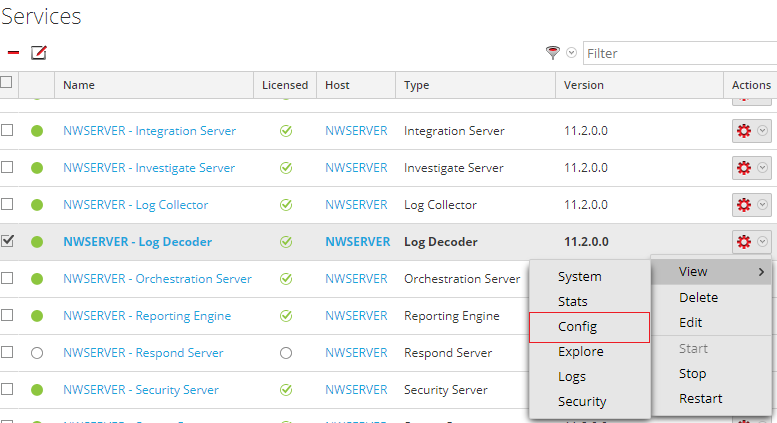
Open Admin > Services on the NetWitness dashboard.
-
Locate the Log Decoder, click the gear to the right, and select View > Config.
-
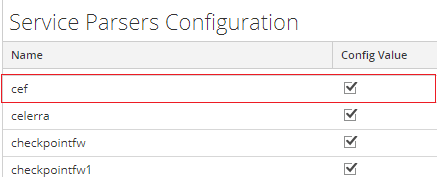
Enable the cef parser in the Service Parsers Configuration and click Apply.
-
-
Edit the CEF configuration to collect NXLog event times.
-
Connect via SFTP using WinSCP or another utility.
-
Locate and back up the XML file at
/etc/netwitness/ng/envision/etc/devices/cef/cef.xml. -
Edit the file, adding the following lines after the end of the preceding
<MESSAGE … />section:<MESSAGE id1="NXLog_NXLog" id2="NXLog_NXLog" eventcategory="1612000000" functions="<@msg:*PARMVAL($MSG)><@event_time:*EVNTTIME($MSG,'%R %F %Z',event_time_string)><@endtime:*EVNTTIME($MSG,'%W-%D-%G %Z',param_endtime)><@starttime:*EVNTTIME($MSG,'%W-%G-%FT%Z',param_starttime)>" content="<param_endtime><param_starttime><msghold>" />
-
-
If required, edit the CEF custom configuration to support custom fields as follows.
-
Connect via SFTP.
-
Locate and back up the XML file at
/etc/netwitness/ng/envision/etc/devices/cef/cef-custom.xml, if it exists. -
Create the file with the following contents. Or if the file already exists, add only the required sections.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <DEVICEMESSAGES> <!-- # # cef-custom.xml Reference: https://community.rsa.com/docs/DOC-79189 # --> cef-custom.xml <VendorProducts> <Vendor2Device vendor="NXlog" product="NXLog Enterprise Edition" device="NXLog_NXLog" group="Analysis"/> </VendorProducts> <ExtensionKeys> <ExtensionKey cefName="Keywords" metaName="Keywords"/> <ExtensionKey cefName="Severity" metaName="Severity"/> <ExtensionKey cefName="SeverityValue" metaName="SeverityValue"/> <ExtensionKey cefName="SourceName" metaName="SourceName"/> <ExtensionKey cefName="ProviderGuid" metaName="ProviderGuid"/> <ExtensionKey cefName="TaskValue" metaName="TaskValue"/> <ExtensionKey cefName="OpcodeValue" metaName="OpcodeValue"/> <ExtensionKey cefName="RecordNumber" metaName="RecordNumber"/> <ExtensionKey cefName="ExecutionProcessID" metaName="ExecutionProcessID"/> <ExtensionKey cefName="ExecutionThreadID" metaName="ExecutionThreadID"/> <ExtensionKey cefName="param2" metaName="param2"/> <ExtensionKey cefName="SourceModuleName" metaName="SourceModuleName"/> <ExtensionKey cefName="SourceModuleType" metaName="SourceModuleType"/> <ExtensionKey cefName="EventReceivedTime" metaName="param_starttime"/> <ExtensionKey cefName="msg" metaName="msg"> <device2meta device="trendmicrodsa" metaName="info"/> <device2meta device="NXLog_NXLog" metaName="info"/> </ExtensionKey> </ExtensionKeys> </DEVICEMESSAGES> -
Locate and back up the XML file at
/etc/netwitness/ng/envision/etc/table-map-custom.xml, if it exists. -
Create the file with the following contents. Or if the file already exists, add the lines between
<mappings>and</mappings>.<?xml version="1.0" encoding="utf-8"?> <!-- # attributes: # envisionName: The name of the column in the universal table # nwName: The name of the NetWitness meta field # format: Optional. The language key data type. See LanguageManager. Defaults to "Text". # flags: Optional. One of None|File|Duration|Transient. Defaults to "None". # failureKey: Optional. The name of the NW key to write data if conversion fails. Defaults to system generated "parse.error" meta. # nullTokens: Optional. The list of "null" tokens. Pipe separated. Default is no null tokens. --> <mappings> <mapping envisionName="severity" nwName="severity" flags="None" format="Text"/> <mapping envisionName="Keywords" nwName="Keywords" flags="None" format="Text"/> <mapping envisionName="Severity" nwName="Severity" flags="None" format="Text"/> <mapping envisionName="SeverityValue" nwName="SeverityValue" flags="None" format="Text"/> <mapping envisionName="dvcpid" nwName="dvcpid" flags="None" format="Text"/> <mapping envisionName="hardware_id" nwName="hardware.id" flags="None" format="Text"/> <mapping envisionName="SourceName" nwName="SourceName" flags="None" format="Text"/> <mapping envisionName="ProviderGuid" nwName="ProviderGuid" flags="None" format="Text"/> <mapping envisionName="TaskValue" nwName="TaskValue" flags="None" format="Text"/> <mapping envisionName="OpcodeValue" nwName="OpcodeValue" flags="None" format="Text"/> <mapping envisionName="RecordNumber" nwName="RecordNumber" flags="None" format="Text"/> <mapping envisionName="ExecProcID" nwName="ExecProcID" flags="None" format="Text"/> <mapping envisionName="ExecThreadID" nwName="ExecThreadID" flags="None" format="Text"/> <mapping envisionName="cs_devfacility" nwName="deviceFacility" flags="None" format="Text"/> <mapping envisionName="info" nwName="info" flags="None" format="Text"/> <mapping envisionName="param2" nwName="param2" flags="None" format="Text"/> <mapping envisionName="SourceModuleName" nwName="SourceModuleName" flags="None" format="Text"/> <mapping envisionName="SourceModuleType" nwName="SourceModuleType" flags="None" format="Text"/> <mapping envisionName="param_endtime" nwName="end" flags="None" format="TimeT"/> <mapping envisionName="param_starttime" nwName="start" flags="none" format="TimeT"/> </mappings>
-
-
Start collecting logs.
-
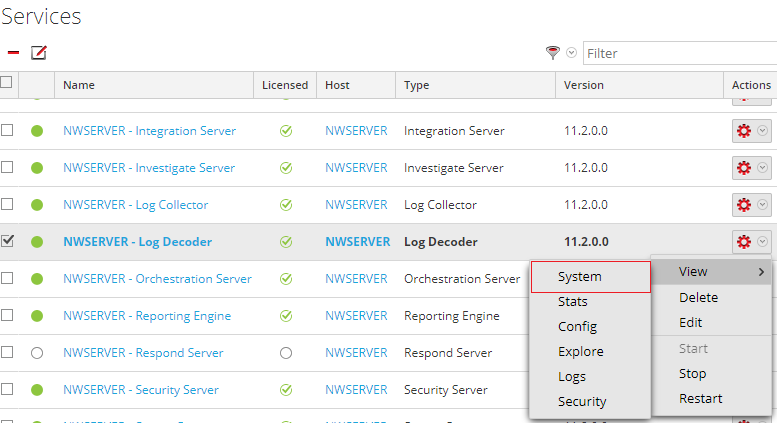
Go to Admin > Services, select the associated Log Decoder, click the gear, and select View > System.
-
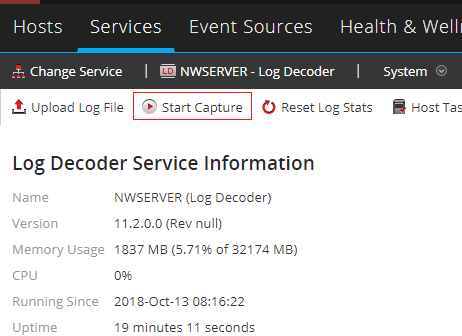
Click Start Capture to start the log collection.
-
Configuring NXLog
NXLog can be configured to collect, convert, and send whatever log events are required. The xm_cef and xm_syslog provide the necessary functionality for converting log data to CEF and adding the Syslog header.
This example configuration reads from Windows Event Log with im_msvistalog, converts the log data to CEF, and forwards it to NetWitness via TCP.
The xm_cef extension module provides the to_cef() function, which generates the CEF format. The xm_syslog extension module provides the to_syslog_bsd() procedure, which adds the BSD Syslog header.
<Extension _cef>
Module xm_cef
</Extension>
<Extension syslog>
Module _xm_syslog
</Extension>
<Input eventlog>
Module im_msvistalog
</Input>
<Output netwitness_tcp>
Module om_tcp
Host 127.0.0.1
Port 514
<Exec>
$Message = to_cef();
to_syslog_bsd();
</Exec>
</Output>To send logs via UDP, use this Output block instead.
<Output netwitness_udp>
Module om_udp
Host 127.0.0.1
Port 514
<Exec>
$Message = to_cef();
to_syslog_bsd();
</Exec>
</Output>Verifying collection on NetWitness
After deploying the NXLog configuration on the log source host and starting the capture on NetWitness, the event log data log should be available on NetWitness.
Go to Admin and select the Log Decoder. In the Events area, select an event to view its details.
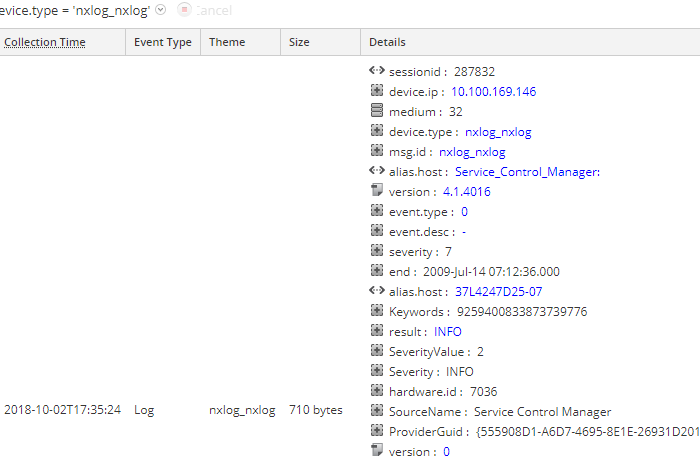
It is also possible to examine the raw log to verify that the output to RSA SIEM is in CEF.
Nov 13 12:34:17 test.test.com Service_Control_Manager: CEF:0|NXLog|NXLog|4.1.4016|0|-|7|end=2018-11-13 12:34:17 dvchost=test.test.com Keywords=9259400833873739776 outcome=INFO SeverityValue=2 Severity=INFO externalId=7036 SourceName=Service Control Manager ProviderGuid={555908D1-A6D7-4695-8E1E-26931D2012F4} Version=0 TaskValue=0 OpcodeValue=0 RecordNumber=3037 ExecutionProcessID=496 ExecutionThreadID=2136 deviceFacility=System msg=The Windows Installer service entered the stopped state. param1=Windows Installer param2=stopped EventReceivedTime=2018-11-13 12:40:28 SourceModuleName=eventlog SourceModuleType=im_msvistalog
