Dell EqualLogic
Dell EqualLogic SAN systems are capable of sending logs to a remote Syslog destination via UDP.
In most environments, two or more EqualLogic units are configured as a single group. This allows storage capacity to be utilized from all devices, and the configuration of RAID levels across multiple drives and hardware platforms. In this case, Syslog configuration is performed from Group Manager and applies to all members.
AUDIT grpadmin 18-Mar-2017 20:13:01.508144 lab-array1 :CLI: Login to account grpadmin succeeded, using local authentication. User privilege is group-admin.
AUDIT grpadmin 18-Mar-2017 20:35:51.833836 lab-array1 :User action:volume select volume1 schedule create test type once start-time 06:30PM read-write max-keep 10 start-date 03/18/17 enable
11501:9173:lab-array1:MgmtExec:18-Mar-2017 20:39:12.115208:snapshotDelete.cc:446:INFO:8.2.5:Successfully deleted snapshot volume1-2017-03-18-20:38:00.3.1.For more details about configuring logging on Dell EqualLogic PS series SANs, check the "Dell PS Series Configuration Guide" which can be downloaded from the Dell EqualLogic Support Site (a valid account is required).
| The steps below have been tested with a Dell EqualLogic PS6000 series SAN. |
-
Configure NXLog for receiving Syslog messages via UDP (see the examples below). Then restart NXLog.
-
Make sure the NXLog agent is accessible from all devices in the group.
-
Proceed with the logging configuration on EqualLogic, using either the Group Manager or the command line. See the following sections.
The following example shows EqualLogic logs as received and processed by NXLog with the im_udp and xm_syslog modules.
<Extension _syslog>
Module xm_syslog
</Extension>
<Extension _json>
Module xm_json
</Extension>
<Input in_syslog_udp>
Module im_udp
Host 0.0.0.0
Port 514
Exec parse_syslog();
</Input>
<Output file>
Module om_file
File "/var/log/equallogic.log"
Exec to_json();
</Output>{
"MessageSourceAddress": "192.168.10.43",
"EventReceivedTime": "2017-03-18 21:12:58",
"SourceModuleName": "in_syslog_udp",
"SourceModuleType": "im_udp",
"SyslogFacilityValue": 16,
"SyslogFacility": "LOCAL0",
"SyslogSeverityValue": 6,
"SyslogSeverity": "INFO",
"SeverityValue": 2,
"Severity": "INFO",
"EventTime": "2017-03-18 21:12:58",
"Hostname": "192.168.10.43",
"SourceName": "11517",
"Message": "380:netmgtd:18-Mar-2017 21:13:19.415464:rcc_util.c:1032:AUDIT:grpadmin:25.7.0:CLI: Login to account grpadmin succeeded, using local authentication. User privilege is group-admin."
}
{
"MessageSourceAddress": "192.168.10.43",
"EventReceivedTime": "2017-03-18 20:35:31",
"SourceModuleName": "in_syslog_udp",
"SourceModuleType": "im_udp",
"SyslogFacilityValue": 16,
"SyslogFacility": "LOCAL0",
"SyslogSeverityValue": 6,
"SyslogSeverity": "INFO",
"SeverityValue": 2,
"Severity": "INFO",
"EventTime": "2017-03-18 20:35:31",
"Hostname": "192.168.10.43",
"SourceName": "11470",
"Message": "88:agent:18-Mar-2017 20:35:51.833836:echoCli.c:10611:AUDIT:grpadmin:22.7.0:User action:volume select volume1 schedule create test type once start-time 06:30PM read-write max-keep 10 start-date 03/18/17 enable"
}
{
"MessageSourceAddress": "192.168.10.43",
"EventReceivedTime": "2017-03-18 20:38:51",
"SourceModuleName": "in_syslog_udp",
"SourceModuleType": "im_udp",
"SyslogFacilityValue": 16,
"SyslogFacility": "LOCAL0",
"SyslogSeverityValue": 6,
"SyslogSeverity": "INFO",
"SeverityValue": 2,
"Severity": "INFO",
"EventTime": "2017-03-18 20:38:51",
"Hostname": "192.168.10.43",
"SourceName": "11502",
"Message": "103:agent:18-Mar-2017 20:39:12.124329:echoCli.c:10611:AUDIT:grpadmin:22.7.0:User action:volume select volume1 snapshot delete volume1-2017-03-18-20:38:00.3.1 "
}This configuration uses a regular expression to extract additional fields from each message.
<Input in_syslog_udp>
Module im_udp
Host 0.0.0.0
Port 514
<Exec>
parse_syslog();
if $Message =~ /(?x)^([0-9]*):([a-z]*):\d{2}-[a-zA-Z]{3}-\d{4}
\ \d{2}:\d{2}:\d{2}.\d{6}:([a-zA-Z.]*):[0-9]*:([a-zA-Z]*):
([a-z]*):([0-9.]*):([a-zA-Z. ]*):(.*)$/
{
$EQLMsgSeq = $1;
$EQLMsgSrc = $2;
$EQLFile = $3;
$EQLMsgType = $4;
$EQLAccount = $5;
$EQLMsgID = $6;
$EQLEvent = $7;
$EQLMessage = $8;
}
</Exec>
</Input>{
"MessageSourceAddress": "192.168.10.43",
"EventReceivedTime": "2017-04-15 16:55:48",
"SourceModuleName": "in_syslog_udp",
"SourceModuleType": "im_udp",
"SyslogFacilityValue": 16,
"SyslogFacility": "LOCAL0",
"SyslogSeverityValue": 6,
"SyslogSeverity": "INFO",
"SeverityValue": 2,
"Severity": "INFO",
"EventTime": "2017-04-15 16:55:48",
"Hostname": "192.168.10.43",
"SourceName": "12048",
"Message": "113:agent:15-Apr-2017 16:57:09.744470:echoCli.c:10611:AUDIT:grpadmin:22.7.0:User action:alerts select syslog priority fatal,error,warning,audit",
"EQLMsgSeq": "113",
"EQLMsgSrc": "agent",
"EQLFile": "echoCli.c",
"EQLMsgType": "AUDIT",
"EQLAccount": "grpadmin",
"EQLMsgID": "22.7.0",
"EQLEvent": "User action",
"EQLMessage": "alerts select syslog priority fatal,error,warning,audit"
}Configuring via the Group Manager
-
Log in to the Group Manager.
-
Go to .
-
Under the Event Logs section, make sure the Send events to syslog servers option is checked.
-
Select the required Event priorities.
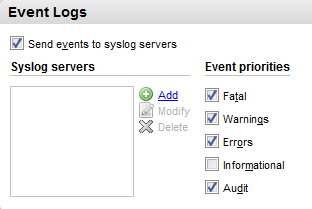
-
Click Add, enter the IP address of the NXLog agent, and click OK.
-
Click the Save all changes button in the top left corner.
Configuring via the command line
-
Log in to the Group Manager via SSH.
-
Run the following commands. Replace
LEVELSwith a comma-separated list of event priorities. Available options include:fatal,error,warning,info,audit, andnone. ReplaceIP_ADDRESSandPORTwith the IP address and port that the NXLog agent is listening on.# alerts select syslog priority LEVELS # grpparams syslog-notify enable # grpparams syslog-server-list IP_ADDRESS:PORTExample 3. Sending logs to a specified hostThese commands will send all logs, except for Informational level, to 192.168.6.143 via the default UDP port 514.
# alerts select syslog priority fatal,error,warning,audit # grpparams syslog-notify enable # grpparams syslog-server-list 192.168.6.143
