Settings
To configure the system components, click on the SETTINGS menu item under the ADMIN menu. Each tab is discussed below.
The Agent manager tab
The agent manager is responsible for connecting to the NXLog agents or accepting connections to establish a secure trusted channel which is used to manage and administer the agents remotely. Each NXLog agent is queried by the agent manager every 60 seconds for status information.
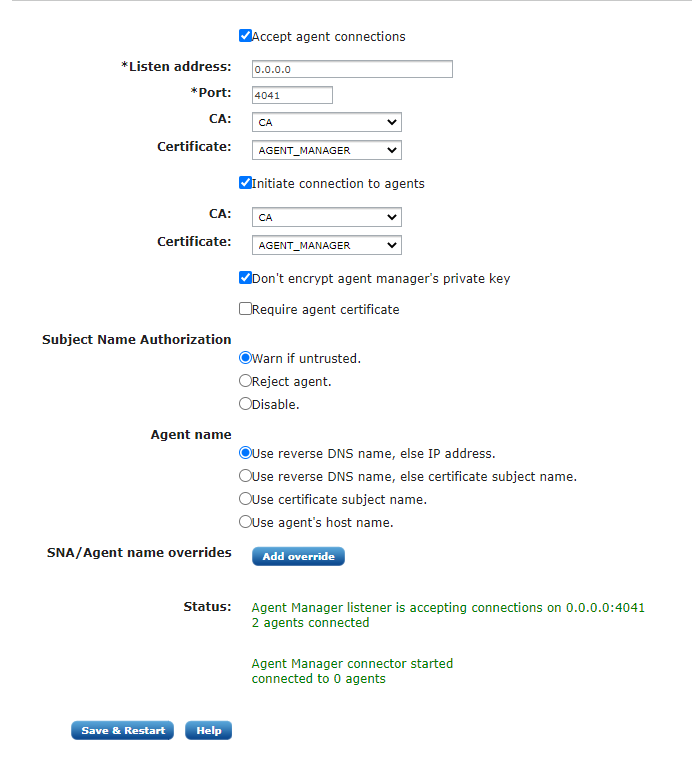
The above screenshot shows the Agent manager tab where its parameters can be configured.
The agent manager can accept and initiate connections to the agents. Enable the Accept agent connections checkbox to let the agent manager accept incoming connections from agents. Enable the Initiate connection to the agent checkbox to let the agent manager initiate the connection.
| For these settings to work, the agents must be configured accordingly. See the Agent Connection type configuration parameter. |
These options have the following configuration parameters:
- Listen address
-
When Accept agent connections are requested, the IP address of the interface must be specified. Both IPv4 and IPv6 types of addresses are supported. Use 0.0.0.0 to listen on all interfaces.
- Port
-
When Accept agent connections are requested, the port number must be specified. This is the port the agent manager will listen to for incoming connections.
- CA
-
The CA configured here is used to verify the certificate presented by the NXLog agent during the TLS/SSL handshake.
- Certificate
-
The certificate configured here will be used to authenticate to the NXLog agent during the TLS/SSL handshake.
For security reasons, certificate private keys in the database of the log
management system are stored in encrypted form. Private key encryption is
carried out with a master key which is accessible to users with the
ROLE_ADMINISTRATOR and/or ROLE_CERTIFICATE access rights.
The agent manager’s private key is required to be able to establish the trusted
control connection with the agents. Enable the
Don’t encrypt agent manager’s private key option for the system to be able to
operate in an unattended mode. Otherwise, the agent manager connection will only
work after a reboot/restart following a successful admin login.
The Subject Name Authorization option refers to the check that happens when the TLS connection is established with the agent and the manager looks at the CN in the certificate subject and checks whether this matches the reverse DNS. This is to prevent malicious agents from connecting with a stolen certificate.
There are 3 options:
- Warn if untrusted.
-
When this option is selected, agent manager will accept agents which try to authorize with Subject Name other than their reverse DNS, and will mark them as
Forged. - Reject agent.
-
When this option is selected, agent manager will reject agents which try to authorize with Subject Name other than their reverse DNS.
- Disable.
-
When this option is selected, agent manager will ignore the mismatch between Subject Name and reverse DNS for connected agents.
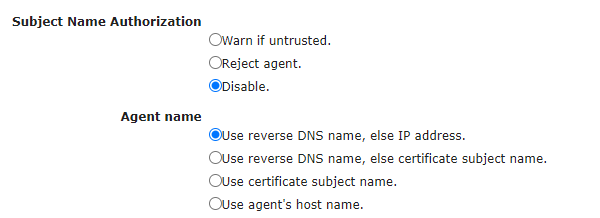
The Agent name setting configures what data to use as the "agent name". Along with Subject Name Authorization, these two options are useful on networks with DHCP assigned addresses where the agent may have different IP addresses.
Due to Subject Name Authorization and the specifics of some networks like NAT, agent manager must have a policy for names of connected agents which will appear on the Agent list. Agent manager supports 3 options for Agent name:
- Use reverse DNS name, else IP address
-
When this option is selected, agent manager will try to resolve the Fully Qualified Domain Name of connected agents. If resolving fails, it will use the agent’s IP address.
- Use reverse DNS name, else certificate subject name
-
When this option is selected, agent manager will try to resolve the Fully Qualified Domain Name of connected agents. If resolving fails, it will use the agent certificate’s Subject Name.
- Use certificate subject name
-
When this option is selected, agent manager will always use the agent certificate’s Subject Name. This option is the only reasonable choice for NAT networks.
| If one of the last 2 options is selected and the NXLog agent does not authorize with valid client certificate (but the manager demands Subject Name), the agent will be rejected. |
Per agent rules for Subject Name Authorization and Agent Name can be defined by clicking the button "Add override". The following dialog will appear:
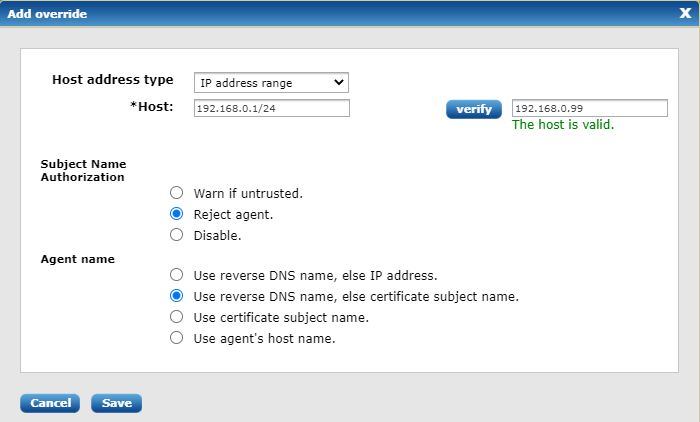
There are 3 types of hosts which can be defined: exact name or IP address; name or IP address regular expression and IP address range. An option exists to verify host definition against real host. The overridden rules will appear as list under the global manager rules.
Later on, these specific rules can be modified and/or deleted.
Click Save & Restart to apply the changes. The Status field will display the status of the agent manager.
The Certificates tab
This tab is divided in two sections: Certificate defaults and Certificates provider.
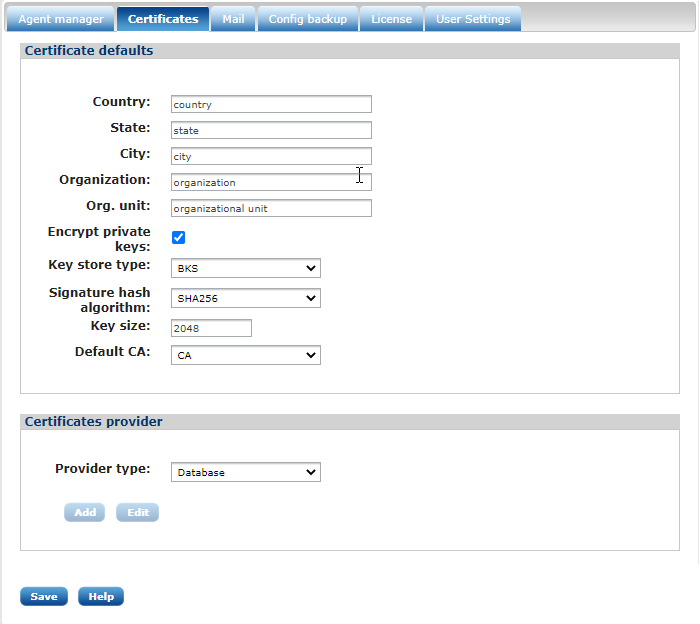
- Certificate defaults
-
This form can be used to set common parameters which are used during certificate creation. Most of these attributes are common, though there are some that deserve a direct mention:
- Encrypt private keys
-
If this is enabled, certificate keys will be stored encrypted in the database. See certificates encryption for more information.
By default on a new system with a blank database, this setting will be disabled. If this setting is enabled, you must always have an available administrator which can unlock the keys after log in. Losing the encryption key will lose access to private keys, making certificates unusable. This feature must be taken very seriously. Practice special care when enabling it. - Keystore type
-
This is the default keystore type that NXLog Manager will use when dealing with certificates. BKS is considered more secure than default Java keystore JKS. If BKS does not have enough support for certificates such as Elliptic Curve Certificates, there is an option to change the keystore type to JCEKS instead.
NXLog Manager uses RSA encryption by default until another type of certificate is used. For example, if EC certificate is imported in the system, EC encryption is used. - Signature hash algorithm
-
SHA256 is the default. The hash algorithm can be changed.
- Key size
-
2048 is the default key size. It is recommended that a longer length be used. Currently, 3072 is considered safe until year 2030 with existing hardware architectures. A length of 4096 is practically unbreakable.
- Certificates provider
-
The Certificates provider option makes it possible to use a PKCS11 compliant backend to store certificates and private keys instead of using the default configuration database. The PKCS11 API is implemented by most smart cards and HSM devices, which can be used to securely store private keys.
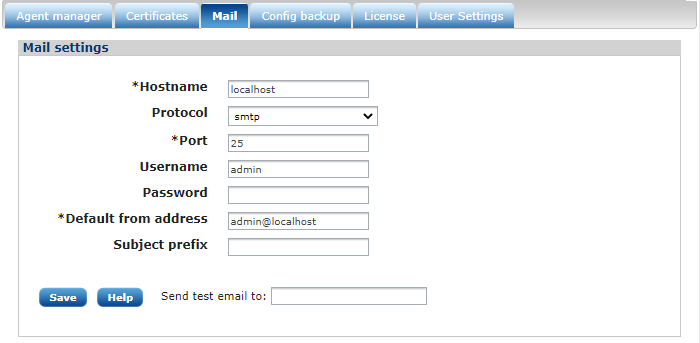
The Mail tab
To be able to send notification emails, an SMTP server is required. The Mail tab provides a form where the SMTP server settings can be specified.
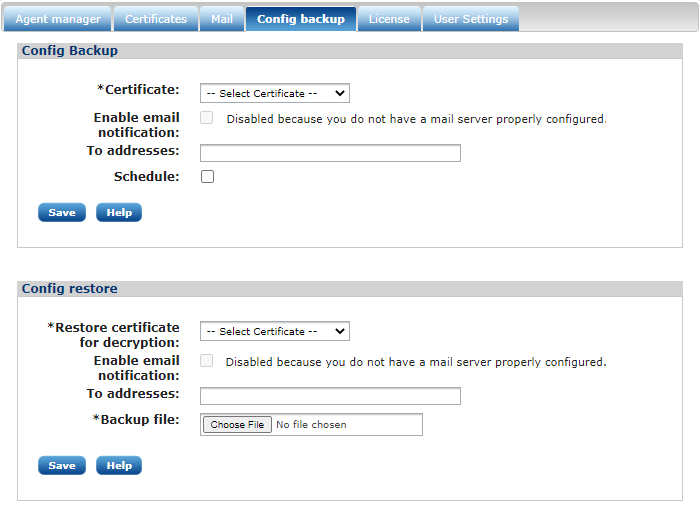
The Config backup tab
The full NXLog Manager configuration can be backed up to an encrypted file. The configuration can be restored using a backup file on the same form. This configuration backup can be scheduled to make it run automatically at a specific time. The system will send an email notification if an email address is provided.
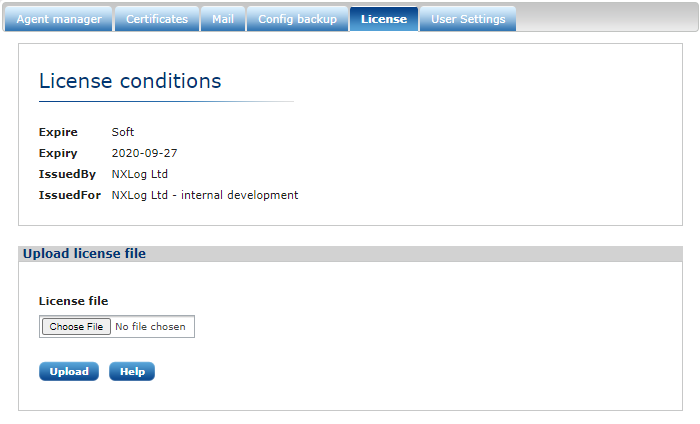
The License tab
The License tab provides a form to upload and show the license file and license details.
If the license is invalid or expired, a warning will be displayed as shown in the following image.

The User Settings tab
This form is divided into the Settings and Change password sections.
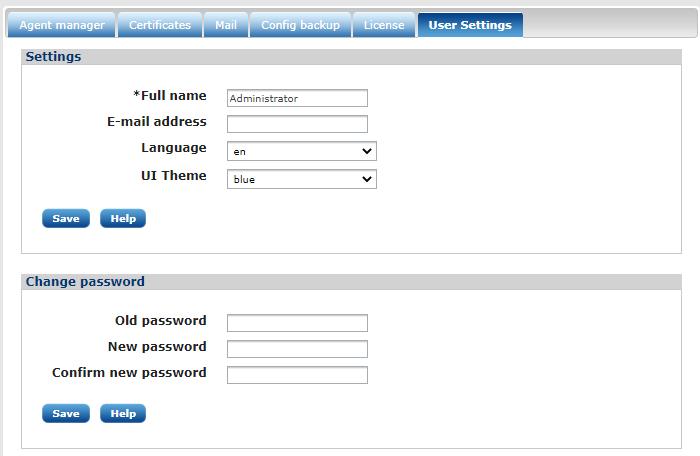
- Settings
-
The logged in user can change their name, email address, user interface language, and theme. The email address will be used for system notifications.
- Change password
-
This section allows to the logged in user to change their password.
