Windows Command Line Auditing
Command line auditing implies monitoring the process with the name A new process has been created on Windows operating systems, and it is carried out for the following processes:
-
Creator process — which runs the command line to create another process
-
New process — which is being created by the creator process
-
Process command line — which contains the path to the new process file and parameters needed to run the new process
This monitoring feature is available starting from Windows Server 2012 R2, see the Command line process auditing section on the Microsoft website. For more information about security, see the Security Monitoring Recommendations on the Microsoft website.
NXLog Agent can be configured to collect and parse command line auditing logs.
| Monitoring of process creation from the command line is also available by utilizing Sysmon, although the native command line auditing solution may be preferable since it does not require the installation of any third-party software. |
The command line process auditing writes events to the Windows Event Log, which can be monitored by capturing event entries with the Event ID 4688.
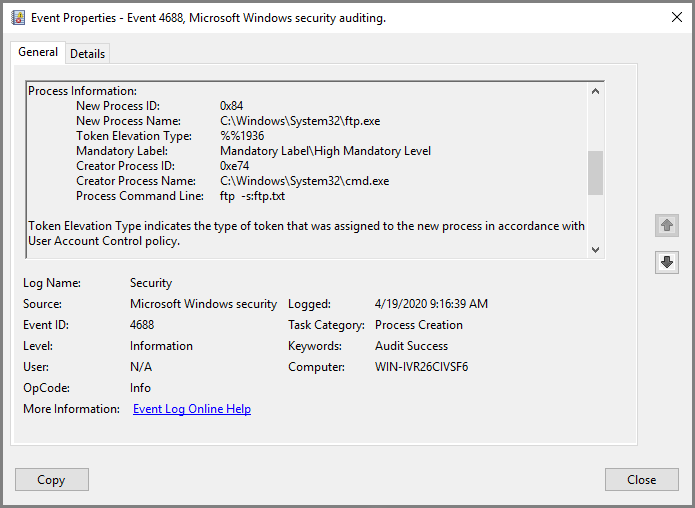
Enabling Command Line Auditing
For various security and usability reasons, command line auditing is switched off by default. Follow the steps below to switch it on.
-
Open the Group Policy MMC snap-in (
gpedit.msc). -
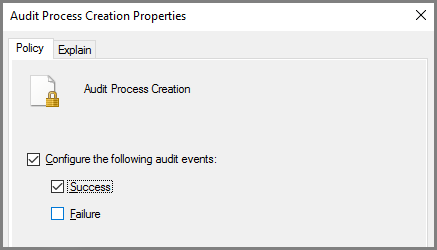
To switch on audit process creation, go to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration > System Audit Policies > Detailed Tracking and open the Audit Process Creation setting, then check the Configure the following audit events and Success checkboxes.
-
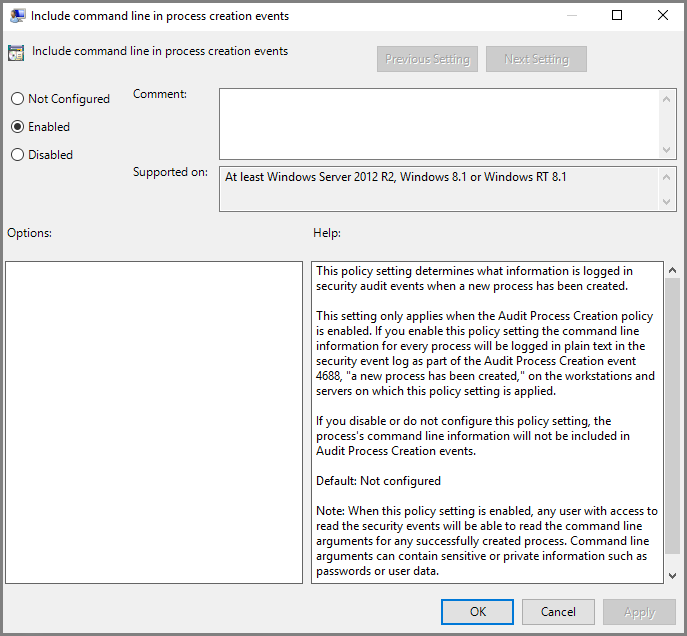
To switch on command line process creation, go to Computer Configuration > Administrative Templates > System > Audit Process Creation, click the Include command line in process creation event setting, then select the Enabled radio button.
-
Reboot the operating system.
For more information about enabling the command line auditing, see How to Determine What Just Ran on Windows Console section on the Microsoft website.
The configuration below demonstrates how to collect Windows Event Log entries
with the ID 4688 of the Security channel to log the activity of the
C:\Windows\System32\ftp.exe application. First, it drops entries without the
ftp.exe substring in the NewProcessName field. After that, the
Message field from the selected entries is deleted to make the example
output shorter. Finally, the logs are converted to JSON format.
<Extension json>
Module xm_json
</Extension>
<Input from_eventlog>
Module im_msvistalog
<QueryXML>
<QueryList>
<Query Id="0">
<Select Path="Security">
*[System[Level=0 and (EventID=4688)]]
</Select>
</Query>
</QueryList>
</QueryXML>
<Exec>
if not ($NewProcessName =~ /.*ftp.exe/) drop();
delete($Message);
json->to_json();
</Exec>
</Input>{
"EventTime": "2020-04-18T16:26:48.737490+03:00",
"Hostname": "WIN-IVR26CIVSF6",
"Keywords": "9232379236109516800",
"EventType": "AUDIT_SUCCESS",
"SeverityValue": 2,
"Severity": "INFO",
"EventID": 4688,
"SourceName": "Microsoft-Windows-Security-Auditing",
"ProviderGuid": "{54849625-5478-4994-A5BA-3E3B0328C30D}",
"Version": 2,
"TaskValue": 13312,
"OpcodeValue": 0,
"RecordNumber": 18112,
"ExecutionProcessID": 4,
"ExecutionThreadID": 3720,
"Channel": "Security",
"Category": "Process Creation",
"Opcode": "Info",
"SubjectUserSid": "S-1-5-21-2751412651-3826291291-1936999150-500",
"SubjectUserName": "Administrator",
"SubjectDomainName": "WIN-IVR26CIVSF6",
"SubjectLogonId": "0x23d19",
"NewProcessId": "0xa24",
"NewProcessName": "C:\\Windows\\System32\\ftp.exe",
"TokenElevationType": "%%1936",
"ProcessId": "0x2a8",
"CommandLine": "ftp -s:ftp.txt",
"TargetUserSid": "S-1-0-0",
"TargetUserName": "-",
"TargetDomainName": "-",
"TargetLogonId": "0x0",
"ParentProcessName": "C:\\Windows\\System32\\cmd.exe",
"MandatoryLabel": "S-1-16-12288",
"EventReceivedTime": "2020-04-18T16:26:50.674636+03:00",
"SourceModuleName": "from_eventlog",
"SourceModuleType": "im_msvistalog"
}