Windows Task Scheduler
Windows Task Scheduler is a system service that allows you to execute automated tasks on a Windows computer. Tasks can be created and managed through the Task Scheduler graphical user interface or the Task Scheduler API.
Task Scheduler is commonly used to perform routine tasks on a system; however, intruders can also use it maliciously to execute code as LocalSystem. On Windows Server 2008 R2 and newer operating systems, a task history is logged to the Windows Event Log. Besides allowing you to identify failing scheduled tasks, collecting and monitoring these events can also help you to detect compromised systems early on.
Enabling Tasks History
Follow these steps to enable logging of Task Scheduler events:
-
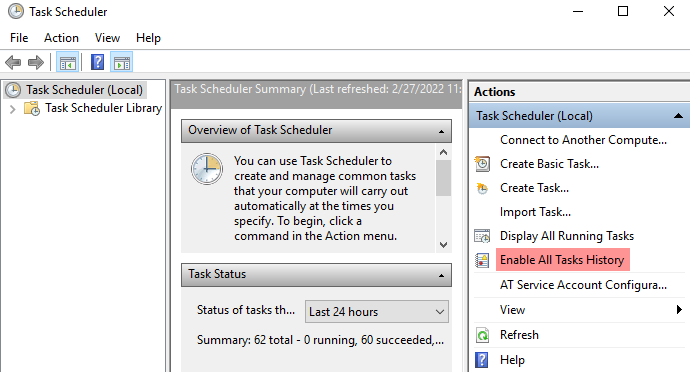
Open Task Scheduler (taskschd.msc).
-
In the Actions pane on the right-hand side, click Enable All Tasks History.
Collecting Task Scheduler events from Windows Event Log
Task Scheduler events are logged to the Microsoft-Windows-TaskScheduler/Operational log.
To verify that this log is enabled:
-
Open Event Viewer (eventvwr.msc).
-
Expand Applications and Services Logs > Microsoft > Windows > TaskScheduler.
-
Right-click on Operational and select Enable Log.
On Windows Server 2012 R2 and newer operating systems, the Microsoft-Windows-TaskScheduler/Maintenance log is also available.
This log contains events related to Task Scheduler maintenance tasks.
For more information, see the Microsoft documentation on Automatic maintenance.
Event IDs
The following events are logged when a task is created or deleted and can help in intrusion detection.
| Event ID | Task Category |
|---|---|
106 |
Task registered |
140 |
Task registration updated |
141 |
Task registration deleted |
142 |
Task disabled |
The following events identify the successful completion or failure of a task.
| Event ID | Task Category |
|---|---|
100 |
Task started |
101 |
Task start failed |
102 |
Task completed |
103 |
Action start failed |
111 |
Task terminated |
129 |
Created task process |
200 |
Action started |
201 |
Action completed |
202 |
Action failed |
203 |
Action failed to start |
See Task Monitoring and Control in the Microsoft documentation for a complete list of monitoring events.
This configuration uses the im_msvistalog input module to collect events from the Microsoft-Windows-TaskScheduler/Operational log.
It then converts log records to JSON format by calling the to_json() procedure of the xm_json module.
<Extension json>
Module xm_json
</Extension>
<Input task_scheduler>
Module im_msvistalog
<QueryXML>
<QueryList>
<Query Id='0'>
<Select Path='Microsoft-Windows-TaskScheduler/Operational'>*</Select>
</Query>
</QueryList>
</QueryXML>
Exec to_json();
</Input>{
"EventTime": "2022-02-27T11:08:08.367566+01:00",
"Hostname": "SERVER-1.example.com",
"Keywords": "9223372036854775808",
"LevelValue": 4,
"EventType": "INFO",
"SeverityValue": 2,
"Severity": "INFO",
"EventID": 106,
"SourceName": "Microsoft-Windows-TaskScheduler",
"ProviderGuid": "{DE7B24EA-73C8-4A09-985D-5BDADCFA9017}",
"Version": 0,
"TaskValue": 106,
"OpcodeValue": 0,
"RecordNumber": 11316,
"ExecutionProcessID": 784,
"ExecutionThreadID": 1292,
"Channel": "Microsoft-Windows-TaskScheduler/Operational",
"Domain": "NT AUTHORITY",
"AccountName": "SYSTEM",
"UserID": "S-1-5-18",
"AccountType": "User",
"Message": "User \"SERVER-1\\jdoe\" registered Task Scheduler task \"\\Malicious Task\"",
"Category": "Task registered",
"Opcode": "Info",
"Level": "Information",
"EventData.Name": "TaskRegisteredEvent",
"TaskName": "\\Malicious Task",
"UserContext": "SERVER-1\\jdoe",
"EventReceivedTime": "2022-02-27T11:08:10.351190+01:00",
"SourceModuleName": "task_scheduler",
"SourceModuleType": "im_msvistalog"
}