Trellix ePolicy Orchestrator
Trellix ePolicy Orchestrator (ePO) enables centralized policy management and enforcement for endpoints and enterprise security products. Trellix ePO monitors and manages the network, detecting threats and protecting endpoints against these threats.
NXLog can be configured to collect events and audit logs from the ePO SQL databases.
| ePO will need to have the associated packages installed first, prior to log collection from these sources, i.e. Endpoint Security. |
Collecting ePO Audit Logs
The Audit log contains Trellix ePO user actions and action details which can be viewed from the ePO dashboard.
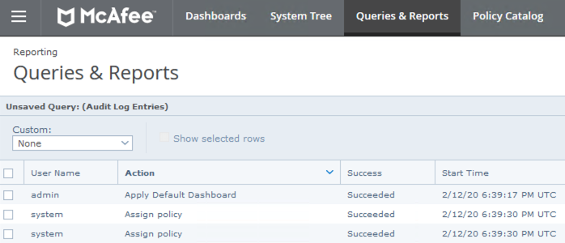
ePO stores these logs in the dbo.OrionAuditLog table in the SQL database.
The following configuration will query dbo.OrionAuditLog using the im_odbc module configured to collect these audit log events.
It will then format them to JSON via xm_json.
<Extension json>
Module xm_json
</Extension>
<Input in>
Module im_odbc
ConnectionString DSN=MQIS;database=ePO_Host; \
uid=user;pwd=password;
IdType timestamp
# With ReadFromLast and MaxIdSQL, NXLog will start reading from the last
# record when reading from the database for the first time.
ReadFromLast TRUE
MaxIdSQL SELECT MAX(StartTime) AS maxid FROM dbo.OrionAuditLog
SQL SELECT StartTime as id,StartTime as EventTime, \
* FROM dbo.OrionAuditLog \
WHERE StartTime > CAST(? AS datetime)
Exec delete($id);to_json();
</Input>EventTime: 2020-02-12 18:36:00
AutoId: 7
UserId: 1
UserName: admin
Priority: 3
CmdName: Logon Attempt
Message: Successful Logon for user "admin" from IP address: 10.0.0.4
Success: TRUE
StartTime: 2020-02-12 18:36:00
EndTime: 2020-02-12 18:36:00
RemoteAddress: 10.0.0.4
LocalAddress: 2001:0:34f1:8072:2c3a:3f1e:f5ff:fffb
TenantId: 1
DetailMessage: NULL
AdditionalDetailsURI: NULL
2020-02-12 18:37:28 McAfeeEPO INFO
id: 2020-02-12 18:37:28{
"EventTime": "2019-07-27T09:51:08.630000+02:00",
"AutoId": 83147,
"UserId": 1,
"UserName": "admin",
"Priority": 3,
"CmdName": "Logon Attempt",
"Message": "Successful Logon for user \"admin\" from IP address: 192.168.134.165",
"Success": true,
"StartTime": "2019-07-27T09:51:08.630000+02:00",
"EndTime": "2019-07-27T09:51:08.630000+02:00",
"RemoteAddress": "192.168.134.165",
"LocalAddress": "192.168.134.165",
"TenantId": 1,
"DetailMessage": null,
"AdditionalDetailsURI": null,
"EventReceivedTime": "2019-07-27T11:51:09.641428+02:00",
"SourceModuleName": "in",
"SourceModuleType": "im_odbc"
}Collecting Endpoint Security events
The Trellix Endpoint Security provides strong virus protection with lower maintenance requirements and zero-impact scans for users to protect against malware.
These events are stored in the dbo.EPOEvents SQL view.
The following configuration uses the im_odbc module to collect events from the dbo.EPOEvents SQL view.
The AnalyzerName column determines the source module of the events in the view; therefore, the query contains the conditional clause AnalyzerName LIKE 'VirusScan%.
<Extension json>
Module xm_json
</Extension>
<Input in>
Module im_odbc
ConnectionString DSN=MQIS;database=ePO_Host; \
uid=user;pwd=password;
IdType timestamp
# With ReadFromLast and MaxIdSQL, NXLog will start reading from the last
# record when reading from the database for the first time.
ReadFromLast TRUE
MaxIdSQL SELECT MAX(ReceivedUTC) AS maxid FROM dbo.EPOEvents
SQL SELECT ReceivedUTC as id,ReceivedUTC as EventTime,AutoID,ServerID,\
AnalyzerName,AnalyzerHostName,\
dbo.RSDFN_ConvertIntToIPString \
(cast (AnalyzerIPV4 as varchar(15))) as 'IPv4',\
AnalyzerDetectionMethod,SourceHostName,\
dbo.RSDFN_ConvertIntToIPString \
(cast (SourceIPV4 as varchar(15))) as 'Source IPv4',\
SourceProcessName,TargetHostName,\
dbo.RSDFN_ConvertIntToIPString \
(cast (TargetIPV4 as varchar(15))) as 'Target IPv4',\
TargetUserName,TargetFileName,ThreatCategory,ThreatEventID,\
ThreatSeverity,ThreatName,ThreatType,ThreatActionTaken,TenantID\
FROM dbo.EPOEvents\
WHERE ReceivedUTC > CAST(? AS datetime) AND AnalyzerName LIKE 'VirusScan%'
Exec delete($id);to_json();
</Input>{
"EventTime": "2019-07-30T14:17:22.067000+02:00",
"AutoID": 22113,
"ServerID": "HOST",
"AnalyzerName": "VirusScan Enterprise",
"AnalyzerHostName": "HOST",
"IPv4": "192.168.134.189",
"AnalyzerDetectionMethod": "OAS",
"SourceHostName": null,
"Source IPv4": "192.168.134.189",
"SourceProcessName": "C:\\Windows\\explorer.exe",
"TargetHostName": "HOST",
"Target IPv4": "192.168.134.189",
"TargetUserName": "DOMAIN\\admin",
"TargetFileName": "C:\\Users\\admin\\Desktop\\eicar.com",
"ThreatCategory": "av.detect",
"ThreatEventID": 1278,
"ThreatSeverity": 1,
"ThreatName": "EICAR test file",
"ThreatType": "test",
"ThreatActionTaken": "deleted",
"TenantID": 1,
"EventReceivedTime": "2019-07-30T16:18:15.279397+02:00",
"SourceModuleName": "in",
"SourceModuleType": "im_odbc"
}Collecting Data Loss Prevention (DLP) events
The Trellix Data Loss Prevention (DLP) Discover Endpoint is a content-based agent solution to inspect user actions. It scans data-in-use on endpoints, blocks the transfer of sensitive data, and can store its findings as evidence.
The configuration below uses the im_odbc module to collect Data Loss Prevention events from the dbo.EPOEvents SQL view.
The AnalyzerName column determines the source module of events in the view; therefore, the query contains the conditional clause AnalyzerName LIKE 'Data%.
<Extension json>
Module xm_json
</Extension>
<Input in>
Module im_odbc
ConnectionString DSN=MQIS;database=ePO_Host; \
uid=user;pwd=password;
IdType timestamp
# With ReadFromLast and MaxIdSQL, NXLog will start reading from the last
# record when reading from the database for the first time.
ReadFromLast TRUE
MaxIdSQL SELECT MAX(ReceivedUTC) AS maxid FROM dbo.EPOEvents
SQL SELECT ReceivedUTC as id,ReceivedUTC as EventTime,AutoID,ServerID,\
AnalyzerName,AnalyzerHostName,\
dbo.RSDFN_ConvertIntToIPString \
(cast (AnalyzerIPV4 as varchar(15))) as 'IPv4',\
AnalyzerDetectionMethod,SourceHostName,\
dbo.RSDFN_ConvertIntToIPString \
(cast (SourceIPV4 as varchar(15))) as 'Source IPv4',\
SourceProcessName,TargetHostName,\
dbo.RSDFN_ConvertIntToIPString \
(cast (TargetIPV4 as varchar(15))) as 'Target IPv4',\
TargetUserName,TargetFileName,ThreatCategory,ThreatEventID,\
ThreatSeverity,ThreatName,ThreatType,ThreatActionTaken,TenantID\
FROM dbo.EPOEvents\
WHERE ReceivedUTC > CAST(? AS datetime) AND AnalyzerName LIKE 'Data%'
Exec delete($id);to_json();
</Input>{
"EventTime": "2019-08-24T12:46:15.603000+02:00",
"AutoID": 94123,
"ServerID": "HOST",
"AnalyzerName": "Data Loss Prevention",
"AnalyzerHostName": "HOST",
"IPv4": "192.168.134.198",
"AnalyzerDetectionMethod": "DLP for Windows",
"SourceHostName": "HOST",
"Source IPv4": "192.168.134.198",
"SourceProcessName": "",
"TargetHostName": "HOST",
"Target IPv4": "192.168.134.198",
"TargetUserName": "DOMAIN\\admin",
"TargetFileName": null,
"ThreatCategory": "policy",
"ThreatEventID": 19115,
"ThreatSeverity": 1,
"ThreatName": "USB",
"ThreatType": "DEVICE_PLUG",
"ThreatActionTaken": "BL|MON|ON",
"TenantID": 1,
"EventReceivedTime": "2019-08-24T14:46:16.066322+02:00",
"SourceModuleName": "in",
"SourceModuleType": "im_odbc"
}

